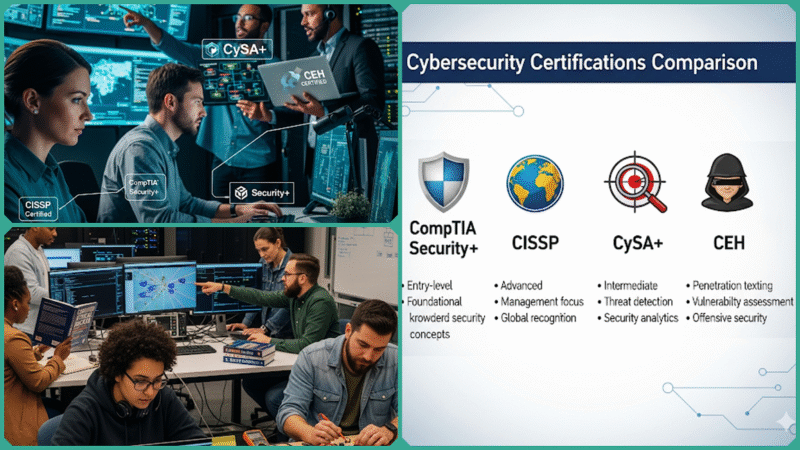
Join our WhatsApp Channel Choosing the right cybersecurity certification can be a pivotal decision for professionals at various stages of their cybersecurity careers. CompTIA Security+
Tag: Digital Security
Join our WhatsApp Channel CEO Fraud Attack is a sophisticated form of Business Email Compromise (BEC) that remains one of the most significant cybersecurity threats
Join our WhatsApp Channel Small and medium-sized enterprises (SMEs) serve as the essential backbone of the global economy, playing a crucial role in driving innovation
Join our WhatsApp Channel In an increasingly interconnected digital world, where cyber threats constantly evolve and data breaches are a daily headline, traditional perimeter-based security